The Threat Indicators Report summarizes the file data-related anomalies on backed-up files. The report also allows you to mark bad or corrupted files so that clean versions of data will be recovered automatically.
To generate the report, Commvault Cloud uses the following techniques to find corrupted files:
-
Threat Analysis: Analyzes backup content in files and file systems to discover possible malware infections. All backup data is recovered to the scanning server, scanned for malware, and then immediately removed from the cache. When malware threats are found, no action is required. The system automatically quarantines these threats so any restore operations will not reinfect the server, thus minimizing the impact of reinfection and impact on your recovery objectives.
-
File Data Analysis: Analyzes backup content for unusual file changes (which can be caused by encryption) and file corruption (which can be caused by ransomware or other threats). File data analysis utilizes several techniques for detection, including reading and previewing files, analyzing files for high levels of entropy, and analyzing SIM hash changes across multiple versions of backed up files. When suspicious files are detected, the user can view these files on the Threat Indicators dashboard,
The following options are available in the upper-right corner of the page in the report:
-
To delete anomalies of a server with unusual file data-related activity, from the client list in the report, click Delete anomaly.
-
To restore a file from a server that has unusual file data-related activity, click Recover files.
By default, the Browse option lists the previous good version of files available in latest cycle. If there are no good versions available in the latest backup cycle, the files are not listed.
The file version prior to the anomaly is recovered.
Report Description
The Threat Indicators Report is divided into tiles, charts, and a table.
Threat Indicators Report Tiles
Total Files
This tile displays the total number of files analyzed on the selected server.
Total Size
This tile displays the total size of the files analyzed.
Suspicious Files
This tile displays the number of suspicious files found.
Suspicious File Size
This tile displays the total size of the suspicious files.
Threats Detected
This tile displays the total number of threats detected (that is, possible malware).
Marked as Corrupt
This tile displays the number of files marked as "Corrupt" on the selected server.
Threat Indicators Report Charts
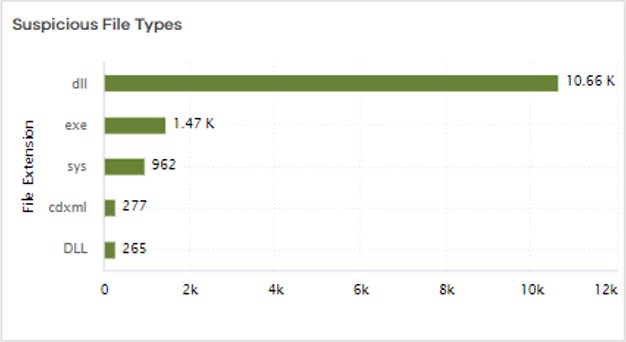
Suspicious File Types
This chart displays the number of suspicious files based on file type.
The following image is an example of the Suspicious File Types chart:
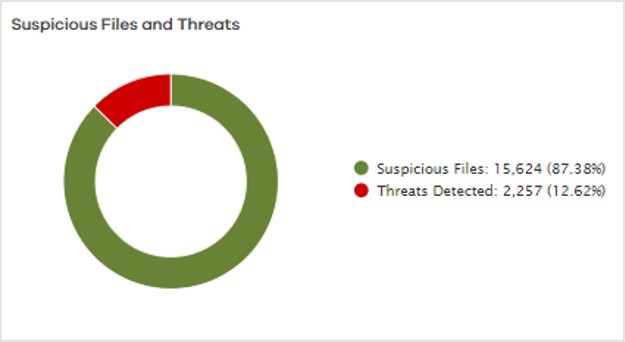
Suspicious Files and Threats
This chart displays the number of suspicious files found and threats detected.
The following image is an example of the Suspicious Files and Threats chart:
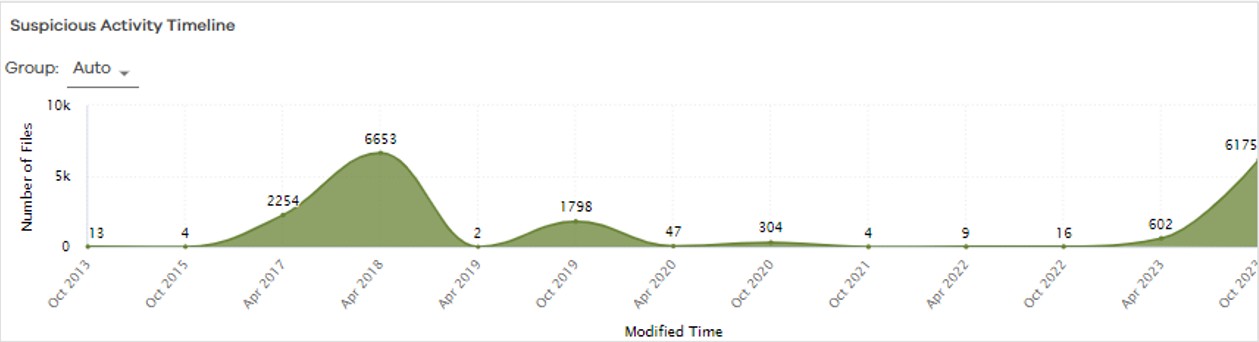
Suspicious Activity Timeline
This chart displays a trending timeline, showing the number of files impacted during a specified time range.
The following image is an example of the Suspicious Activity Timeline chart:
Suspicious Files Table
The following table includes descriptions of columns in the Suspicious Files table.
|
Column |
Description |
|---|---|
|
File Path |
The path to the affected file. |
|
Versions |
The number of versions of the affected file. |
|
Actions |
|
To see all file versions for a set of files, click the down arrow  next to a file path. The following columns will appear in the Suspicious files sub-table:
next to a file path. The following columns will appear in the Suspicious files sub-table:
|
Column |
Description |
|---|---|
|
File name |
The path to the affected set of files. |
|
Modified time |
The number of file versions analyzed. |
|
Suspicious |
Indicates if the system identifies the file as suspicious. |
|
Marked corrupt |
Indicates if a user has already marked a version of file corrupt. |
|
Backup job ID |
The ID of the backup job that backed up that file. |
|
Actions |
|
To see detailed information for a file, do the following:
-
Click the name of the file.
A window appears, showing a preview of the file (if available), the status of the file, the entropy value, the file path, the file's modified time, the backup job ID for the file, and the file's owner.
Note
The entropy value is displayed only if the file's entropy value is 6 or higher (on a scale from 1 to 8).
-
To download the file to your computer, click the Download button (if available).
 , and then click Restore.
, and then click Restore.