Applies to: MSP administrators and tenant administrators
When you use identity and security authentication applications like Jamf Connect instead of Active Directory for Mac laptops, you must create an automatic server group and apply settings for accurate laptop owner assignment. The settings allow the system to correctly assign ownership by retrieving user information from the Mac laptop.
Important
This procedure does not apply to laptops using the Windows operating system. To automatically map Windows laptops to owners, see Automatically Map Windows Laptops to Owners.
Procedure
-
To group laptops with macOS, create an automatic server group.
-
From the navigation pane, go to Manage > Server groups.
The Server groups page appears.
-
In the upper-right corner of the page, click Add.
The Add server group dialog box appears.
-
In the Name box, enter a name for the server group.
-
Select Automatic Association.
-
From the Client Scope list, select Clients of company.
The Company list appears.
-
Select the company for which you are creating an automatic server group for Mac laptops.
-
To add the rule to automatically group laptop clients in the company, beside Rule groups, click Add rule group.
The Edit associations dialog box appears.
1. From the Select rule type list, select Client.
2. From the Which matches with list, select equal to.
3. From the Value list, select Laptop Client.
4. Click Save.
-
To add the rule to automatically group macOS computers in the company, beside Rule groups, click Add rule group.
The Edit associations dialog box appears.
1. From the Select rule type list, select OS Version.
2. From the Which matches with list, select contains.
3. From the Value list, enter macOS.
4. Click Save.
-
Click Save.
-
-
To identify the laptop users as owners, configure the following settings for the server group:
-
sLaptopUserDomain: This setting defines the domain where the users are registered, and the value must match the company's identity server name.
-
sLaptopUserDomainEmailSuffix: This setting defines the email address of the users, and the value must match the email suffix for the company's identity server in the following format:
@<email suffix>Tip
To find the exact email suffix, navigate to the company's identity server page under Manage > Security and click the Associations tab. The email suffix appears in the Email suffixes section.
-
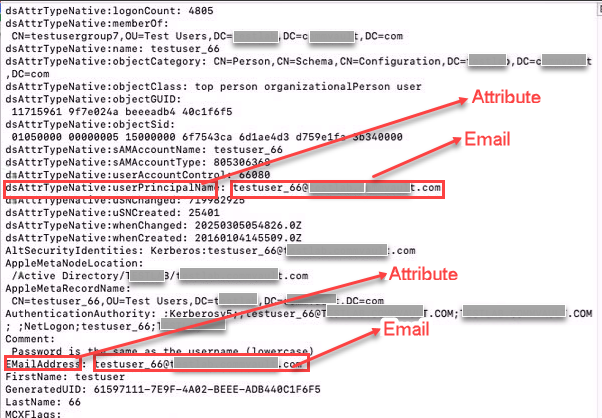
sLaptopUserDomainEmailKey: This setting defines the attribute that stores the users' email addresses. And, the value must match the attributes storing your email address in the terminal results for the following command:
dscl localhost -read /Search/Users/<username>To determine the attribute storing the email address:
-
execute the following command in the terminal:
dscl localhost -read /Search/Users/<username>Where, the username is the one you used to sign into the Mac laptop.
-
In the results, run a search for your email address and copy the attribute with your email address. Use this attribute as the value of the sLaptopUserDomainEmailKey setting.
In this example, the attribute values can be EmailAddress or dsAttrTypeNative:userPrincipalName:
-
Enter the attribute as the value of the sLaptopUserDomainEmailKey setting. In the example, EmailAddress or dsAttrTypeNative:userPrincipalName can be the setting value.
-
-
Results
These server group settings are pushed to the Mac laptops and used to assign the logged-in user as the owner automatically. Furthermore, the user is identified as the laptop owner in the Edge Monitor application without needing any authentication.